The headline on the front page of the Sunday Vision screamed, PANIC AS NATIONAL ID DATA IS STOLEN. I dropped all I was doing to quickly get myself a copy of the news paper. Being one of those people that have continuously cautioned our government over its handling of electronic data, I was only too eager to see what had been done wrong this time round.
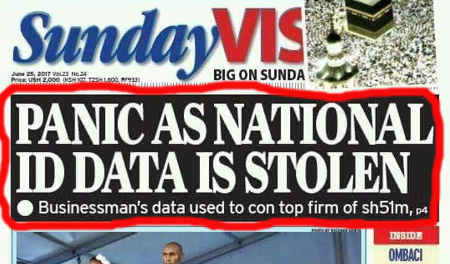
The screaming Sunday Vision Headline
The title of the article gives one the impression that the folks at the National Identification and Registration Authority (NIRA) were caught napping on duty.
In the article, a one Norbert Kamwebaze was allegedly paid twice for work he did for Roko Construction with the second payment being dished out to an imposter who presented an ID card to Roko that had all his details save for a difference in the face.
The article starts off with a clear indication of the agenda the authors had; “Panic has gripped members of the public after it emerged that confidential data that Ugandans submitted to NIRA could have landed in wrong hands….” Using a very basic example, we have had forgery of permits for a long time in this country where someone lifts all the information of a legitimate permit and only changes the face to reflect his. Why has there never been any doubt cast on Face Technologies over our data? I was irked by the quick conclusion being insinuated in the article yet the details of the story indicate that suspicion should first be cast elsewhere.
Let us look at the issues raised so far and what they mean;
-
Mr. Kamwebaze was contracted by Roko construction to do a job for UGX 51 Million Shillings
-
Upon completion of the job, he was paid in full but not before producing proof of his identity by presenting a National ID which was duly photocopied.
-
Mr. Kamwebaze proceeded to bank the cheque on his account in Barclays bank and it was cleared.
-
A few days later, another person bearing a similar ID appeared at Roko for payment and was issued a cheque for payment.
This is where the story gets an interesting twist. Roko as a company has decent accounting systems in place with well set processes and procedures. I have done work for them before and know that the point persons one deals with when it comes to finances are limited and they usually know even off head who has been paid. The issuance of cheques follows some fairly lengthy procedures and this makes me wonder how a second cheque could have been issued without internal connivance. Is it possible that by coincidence all those who handled the first payment issued were never available when the impostor turned up?
-
The double payment was discovered by the Roko top management.
This is already a pointer that the lower level staff have some serious questions to answer.
-
The impostor opened up an account with the same bank, Barclays using the same bio data as Mr. Kamwesigye, went ahead to ensure the account had the same bank balance as that of the legitimate Kamwesigye and two days later, deposited the cheque of 51 Million. Upon maturity, he withdrew all the money.
This raises some interesting questions. They are:
-
Could it be that the banking software used by Barclays has no ability to detect duplicates? How could two accounts with similar bio data exist yet having different photographs? Shouldn’t a flag have been raised internally at least first with the Systems Security team?
-
How did the impostor get to know the details on the legitimate Kamwesigye’s account including bank balance? Was he working with an insider in Barclays? Could there have been collusion between Mr Kamwesigye and this alleged impostor?
Back to the National ID, no where in the article does it indicate the trail to NIRA. There is a presumption that the NIRA database could have been hacked to get this information but this does not appear to hold much water considering that there are still many other ways one would have accessed this ID information. Based on my assessment, these are the first areas of suspicion before casting NIRA in bad light:
-
The impostor could have worked with staff at Roko who availed him the ID information since they already had a photocopy and considering that he picked his money after the real claimant had already got his.
-
The real Mr. Kamwebaze could have connived with the impostor and come up with the new ID that the impostor used.
-
The impostor could have tracked Mr. Kamwebaze and been able to get access to his National ID without his knowledge. Thereafter, he hatched out his plan.
At this point, unless further information is availed showing complicity by NIRA, I am inclined to believe that this was more of social engineering than hacking into the National ID Database.
It is on this note that I would like to register my disappointment with the New Vision for falling prey to the sensationalist headline approach typical of the reckless Ugandan tabloids.
One positive though the article brings out is the need for our public institutions to guard against data pilferage. Remember, the weakest link in any IT systems is the human being. Employ professionals who know what they are doing and are willing to stand by a pre-set code of ethics. We shall minimise the likely occurrence of such.
Eid Mubarak to my Muslim brothers and sisters.
James Wire is a Technology and Small Business Consultant based in Kampala, Uganda
Follow @wirejames on Twitter.
Email lunghabo [at] gmail [dot] com


 Accessing the free WiFi in Kampala entails being within an area that has the signal hence allowing your phone or mobile gadget to connect. The hotspots have been spread in certain locations for starters with others to follow suit later. As a first time user, you are expected to submit some profile information and then get access thereafter. In keeping with the expectations of Hon. Father Lokodo the State Minister for Ethics and Integrity, no pornography shall be accessible.
Accessing the free WiFi in Kampala entails being within an area that has the signal hence allowing your phone or mobile gadget to connect. The hotspots have been spread in certain locations for starters with others to follow suit later. As a first time user, you are expected to submit some profile information and then get access thereafter. In keeping with the expectations of Hon. Father Lokodo the State Minister for Ethics and Integrity, no pornography shall be accessible.